Millenials and Gen-Zers have grown up familiar with the ins and outs of the internet. Before Facebook and Twitter, Millenials were warned that when they entered online chatrooms, they should be sure not to give too much personal information, don’t share your real name, and to never meet up in person with someone they’ve met on the internet. These internet safety rules seem foreign now that the same generation is that which uses Facebook, shares their lives daily with Snapchat, and takes rides from strangers on the regular with Uber. So why is internet safety important? If you’re sharing this much now, things must be different, right?
As a small business owner, you have to be aware of the risks you are taking with the internet. According to CNBC, 14 million US Businesses are at risk for a hacker threat. Yet, only 2 percent of small business owners view the threat of cyber attack as the most critical issue that they face.
Why is internet safety important?
It’s happened to Target: 110 million customers’ personal and financial information was exposed in 2013. Chipotle’s payment system was hacked earlier this year and millions of their customers had their credit card information stolen. And, y’all. We’re not even safe from #spoileralerts. Hackers obtained 1.5 terabytes of data from HBO less than a month ago. And now they’re out there spilling the beans on the upcoming Games of Thrones episodes. What is the world coming to? These examples only touch on a few of the biggest corporate hacks in history.
If you think that because your business is small, you’re in the clear, you’re misinformed. These large companies with millions of stolen customer data and dollars are just what hits the headlines. Hackers find “the little guy” businesses of interest because they’re aware that small businesses are less likely to have the resources to implement high-end cybersecurity protection.
Your small business could be their next target.
Still Wondering ‘Why is Internet Safety Important?,’ Here are the Facts:
StaySafeOnline.org has many resources for understanding small business internet security threats. On their website, they also include the following data on considerable risks that are often not addressed:
- 77% do not have a formal written Internet security policy for employees.
- 63% do not have policies regarding how their employees use social media.
- 60% say they have a privacy policy in place that their employees must comply with when they handle customer information and half (52%) have a plan or strategic approach in place for keeping their business cyber secure.
- More small business owners say they do not (45%) provide Internet safety training to their employees than do (37%).
- Two thirds (67%) allow the use of USB devices in the workplace.
- Six in ten (59%) say they do not require any multi-factor authentication for access to any of their networks, and only half (50%) say that all of their machines are completely wiped of data before disposal.
Internet Safety Threats
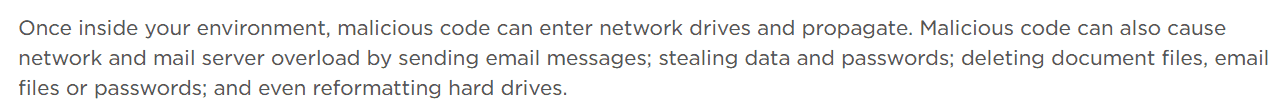
Malicious Code

Photo Credit: Richard G.
Malicious code is any code in any part of software program or script written to do harm. Examples of malicious code include computer viruses, worms, trojan horses, logic bombs, spyware, adware and backdoor programs. This is an application security threat that cannot be controlled by conventional virus software.
Lost or stolen devices
Did you know that data shows that every 53 seconds, someone’s laptop gets stolen? This generally happens in bars and while using public transportation. There have been many technological advances over the last ten years that have helped in guarding your data from thieves, but we keep so much of our lives inside our virtual files that it can still be a tragic loss.
A writer on The Guardian describes what he learned when his laptop was stolen, including some programs to have installed in case it happens to you. We’ll discuss those, along with preventative techniques later on in the article.
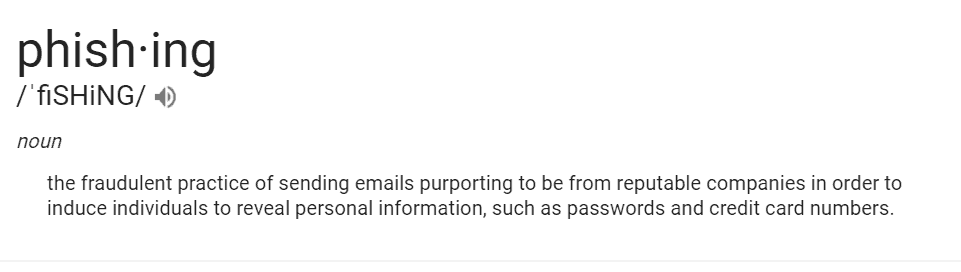
Spear Phishing
No, not spearfishing, spear PHishing. You may know spear phishing’s close relative, phishing.
Well, spear phishing is the latest spin on this internet safety threat. Rather than looking like a reputable company that is looking to get your personal information, someone who is spear phishing already knows a little bit about you. They pose as a family member or a friend and already know your name, email address, and some basic information. They then use those bits of information as a mask of familiarity to gain more personal information.
Where do they get this information? Your web presence and social media profiles. Their goal is to build trust and eventually uncover what could be your password to your financial accounts.
Unsecured Wireless Networks
If your employees use their laptop, tablet or smartphone for work outside of the office, they should wary of using public internet sources. There’s plenty of news stories to back up the dangers of using unsecured wireless networks. Hackers have been known to steal data from hotels and convention centers, retail chains and even the WiFi network of an entire city. There are so many security dangers with using public WiFi. Watch the video below to learn how hackers use unsecured wireless internet networks to steal your public information.
As the video mentions, if you do use public wifi, you should first verify the wifi network with an employee. It’s also helpful to turn off sharing and use a VPN.
Insider Threats
A threat to your company’s security could be sitting just a few desks away from you. We’ve mentioned before that it’s difficult to find good employees, taught you how to hire quality employees, and how to train them. But, things could still go wrong after that. According to Tripwire.com, insider threats are the main security threat in 2017. Not all of the issues lie with those who are disgruntled and malicious. But between careless mistakes, phishing traps, and angry employees, there is a lot that can go wrong.
“Among 874 incidents, as reported by companies to the Ponemon Institute for its recent 2016 Cost of Data Breach Study, 568 were caused by employee or contractor negligence; 85 by outsiders using stolen credentials; and 191 by malicious employees and criminals.”
Insider threats are hard to distinguish and can go on for years. Not only that, but it is easy for an employee to cover their actions and difficult for the employer to prove their guilt.
Tips for Small Businesses to Improve Internet Safety
You may not be able to shell out the cash for the same extensive security systems that large companies can, but you can do many things to defend your company and your customers from becoming a target. The following tips should help safeguard you from hackers and be aware of the places that they hide. After all, they’re not walking around in plain sight like this:
1. Educate your team
Your team should be aware of the risks of not having internet safety protocols in place. Teach them about the safety threats listed above and make sure that there are consequences in place for those who do not take internet security measures seriously. Remember, employee apathy is a huge threat to your business. Teach them about phishing and why your company uses certain security measures. It’s worth the time and investment to educate your employees about internet safety, reinforce the risks of weak security habits and instill good habits on topics such as password hygiene, downloading content, and sharing information online.
2. Don’t click that!
Always be suspicious of file links. Email fraud happens frequently and spambots and hackers have even starting sending text messages encouraging their victims to click links and phish for their personal information.
Phishing happens frequently. It’s important to alert your employees and to show them some of the signs of a phishing email. Lastpass even encourages small business owners to send out fake phishing emails to all of your employees to see who clicks and who reports the suspicious activity. Consider it like a fire drill, but a phishing drill.
3. Lock all your Devices
…and throw away the key, the risk is just too high!
I kid, I kid. But your internet safety protocol should extend to every device that your employees use for work. Your employees should have their phone password protected and should change that password after they’ve had the same one for long.
4. Be smart with passwords
You’re not helping your cause if you enforce password protection but insist on having the password of choice to be ‘password,’ ‘123456,’ ‘qwerty’ or any of the most commonly used passwords. You can check the strength of potential passwords through Microsoft’s Safety & Security Centre Password Checker. On top of that, two thirds of people use the same password for multiple, or even all of their accounts? This makes it easier for someone on your team who allowed a breach of security in their personal life to affect your business.
Create a password policy within your company that disallows use of the same password, mandatory password changes, requirements for strong passwords, and when neccessary, a two-step authentication process. If your employees find it difficult to remember many passwords, we suggest using a secure password manager like LastPass.
5. Use a tracking app for your devices
Remember earlier when I mentioned the author, Keith Stuart who lost all his files when his laptop was stolen? He suggests using a tracking service app like Prey, LockitTight or LoJack. Each of these allow you to remotely wipe your device clean of your files and personal data, which could include the financial information for your business and customers.
You can also find out the IP address of whoever stole your laptop. Or, if you’re a Mac user, you can use the iCloud to locate your device. But, heed Stuart’s advice:
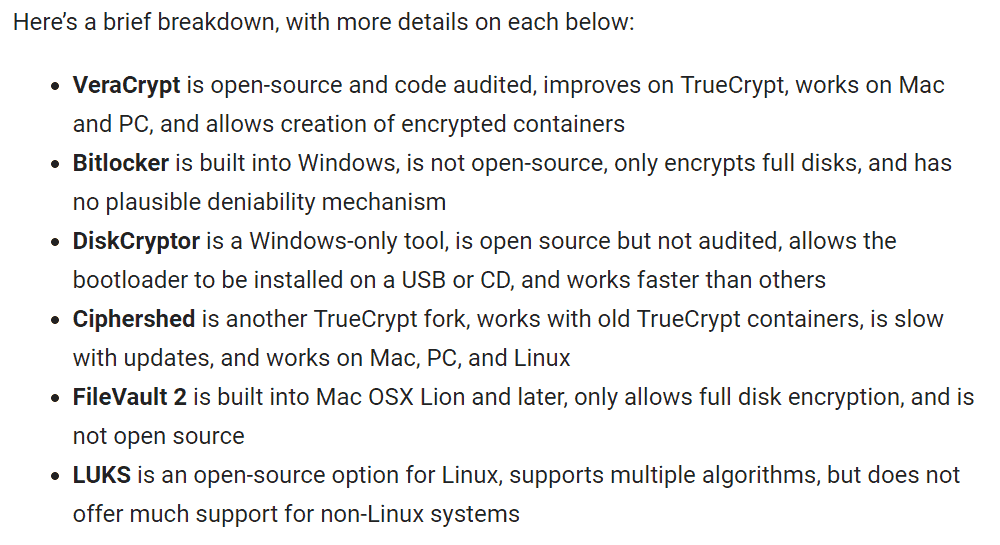
6. Encrypt , encrypt, encrypt!
If encryption sounds like a medieval disease to you, don’t worry, we’ve got you covered. Encryption is a method of turning data into code to prevent those without authorized access from obtaining your information. When you’re internet shopping from a secure site, they encrypt your credit card information. You can do the same with files on your computer and the files will require a password before viewing them.
Encryption isn’t 100% foolproof, but it’s better than leaving your files completely vulnerable. Encryption programs encode data or make it unreadable to outsiders, until you enter a password or encryption key. Comparitech.com has a list of encryption software you can get at low or no cost.
7. Use a reliable security solution
Not all anti-virus software is created equal. You must use the most up-to-date versions of security suites, and ensure that they have all of the capabilities you’ll need for your business. These include, but aren’t limited to: firewall protection, anti-spam, back up, tune up, and protection against phishing sites. Check out PCmag.com’s roundup of the Best Security Suites of 2017.
Apply this to your small business
Despite a lack of media coverage, small businesses are very mush at risk for internet security threats. And, unfortunately, when hit hard, small businesses just don’t have the capital to withstand security breaches in the same way that large companies do. Remember that as a small business owner, you’re still at risk for hackers and phishing scams, more so than the average person. Because of this, there must be layers of security measures in place across your company.
Not having security measures in place risks more than money. It could cost you your entire business. The amount of money that hackers can steal may be more than you’re able to withstand, and if your customers’ data is breached, they will lose confidence in your company. Fewer dollars in the bank and fewer customers could devastate you.
Now, give this a try:
Create a cohesive internet security plan with all of this information in mind. Add this to your standard operating procedures and check in with your security software and protocols often. Hackers are consistently finding new ways to steal information, so you should consistently be on the defense.
Did you find this post on why internet security is important helpful? Subscribe to our blog for weekly small business tips and resources.













[…] Source: http://www.apolloansweringservice.com […]